
How to use Windows Ransomware Protection
— GhostVolt Research —
What is Ransomware?
At this point we all know what ransomware is and the effect it can have on you or your business (if you don’t know, head over to your favourite news channel and peruse the technology section). But what is not so well known is the latest “trendy” way in which cybercriminals are using ransomware to blackmail you into paying ransoms.
That trend is to simply steal all your data which is then used to blackmail you into paying a ransom. If you do not pay-up, your data its leaked on the internet, used for identity theft or just sold to the highest bidder.
So now, not only do we have the threat of our files being encrypted until we pay a ransom for a ‘decryption key’, but we also have the very scary prospect of all your data being stolen and held to ransom.
Windows Ransomware Protection?
Did you know your copy of Windows 10 has Ransomware protection built in? You’re not alone; Windows Ransomware Protection is still largely unknown and overlooked, but it’s super simple to set up and protects you against traditional ransomware attacks which encrypt your files and hold them hostage.
Controlled folder access.
Windows Ransomware Protection is a Windows 10 feature known as “Controlled folder access” which protects files, folders and memory areas on your computer from unauthorized changes by suspicious or malicious apps including malware and ransomware. It is especially useful in helping protect against ransomware that attempts to encrypt your files and hold them hostage.
Controlled folder access works with a list of trusted apps. Apps that are included in the list of trusted software work as expected. Apps that are not included in the list are prevented from making any changes to your files inside protected folders and will stop cybercriminals from encrypting your files and demanding you pay a ransom for the “decryption key” to unlock them.
Learn more about Windows Ransomware Protection
Does Windows Ransomware Protection stop cybercriminals from reading my files?
No! Remember, Windows Ransomware protection prevents your files from being changed by unauthorised or malicious Apps, but they can still be read or copied by an attacker. This means you’re still vulnerable to your data being stolen and held to ransom. To prevent cybercriminals from reading your data, you should enlist the help of File Encryption.
File encryption
Encrypting your files is a critical part of your defence against cybercriminal attacks, including ransomware. When your files are encrypted, criminals cannot access your data. Instead, they can only see scrambled nonsense (random letters, numbers and symbols) which is useless to them and therefore cannot be used for extortion or to hold you to ransom.
Product plug alert!
If you don’t already use a file encryption solution, why not take GhostVolt for a free 30 day, no obligation trial? With GhostVolt, all your files are automatically encrypted with 256 AES industry standard encryption and because it works just like Windows File Explorer, its super is to use - you probably already know how to use it!
If you’d prefer to use another file encryption product, that’s cool too. Google “File encryption software” and choose an App that works for you. Just make sure you’re securing your files before moving onto the tutorial below.
How to set up Ransomware Protection
In the following tutorial we’ll assume you have GhostVolt installed to encrypt your files and data. Let’s take a look how we can use Windows Ransomware Protection and GhostVolt to defend you against malware and ransomware threats.
Active Windows Controlled folder access
1. Click the Windows icon and type “Windows Security” and click Windows Security.
2. Choose Virus & threat protection.
3. Navigate to the Ransomware protection section and and click Manage ransomware protection.
4. Turn on Controlled folder access.
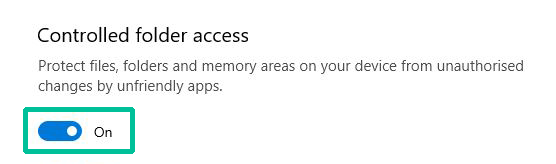
When activated, Windows system folders are protected by default.
Protect your GhostVolt repository
Now that you’ve activated Controlled folder access, you’ll need to add your GhostVolt repository folder to the protection list. Note: Your repository will be named “GhostVolt” and located in the place you specified when setting up the GhostVolt application.
1. Click Protected folders.
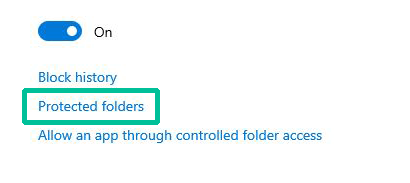
2. Click Add a protected folder and navigate to your GhostVolt repository, select it and confirm with the Select Folder button.
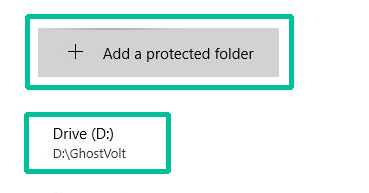
If everything has gone to plan, your GhostVolt repository is now being protected by Windows Ransomware Protection. We now need to add GhostVolt and associated Apps to the list of trusted Apps.
Allow GhostVolt through Controlled Folder Access
1. Click the Back arrow in the top left and choose Allow an app through controlled folder access.
2. Click Add an allowed app > Browse all apps.
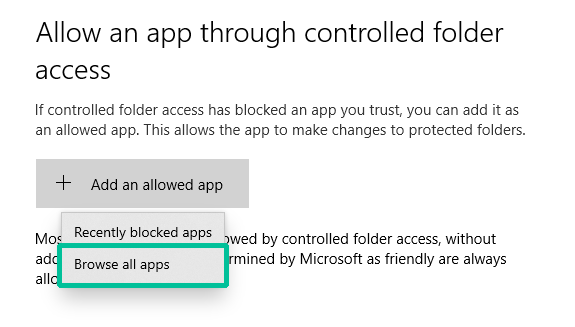
3. Navigate to your GhostVolt application (wherever the app is installed, in my case it’s in C:\Program Files (x86)\GhostVolt). And choose GhostVolt.exe
Repeat steps 2 and 3 until you have the following in the Allow an app through controlled folder access list:
- GhostVolt.exe
- GhostVoltFileController.exe
- GhostVoltFileMonitor.exe
- GhostVoltService.exe
Please make sure you add all the above files to the Trust list, failure to do so will cause GhostVolt to stop working correctly and will leave your defences open to attack.
That’s it! You’re all done. You’re now protected with Windows Ransomware and GhostVolt file encryption.
Now that I’m protected, what will happen if my PC is infected?
In the case that the malicious application attempts to change any of your Protected Folders, Windows security will simply block the operation and you will get a desktop notification: “Unauthorised changes blocked”. And since your files are encrypted with GhostVolt, the attacker does not have access to your data and cannot hold it to ransom.
Wait... Don't forget to backup your files too!
Backups are the most effective way of recovering your files and data from a ransomware attack, so it's crucial you have a backup plan. Should you be the victim of an attack and you do not have any backups, you will be left with no option other than to pay the ransom, or lose your files forever.
Tips for backing up your files
- Make regular backups of your most important files. Ideally your backups should be fully automated.
- Ensure you create offline backups that are kept separate, in a different location as ransomware actively targets backups.
- If you are using cloud backups, ensure that your cloud service protects previous versions of the backup from being immediately deleted and allows you to restore to them. This will prevent both your live and cloud-backup data becoming inaccessible.
- Make sure that the devices containing your backup (such as external hard drives and USB sticks) are not permanently connected to your network. Attackers will target connected backup devices and solutions to make recovery more difficult.
- Ensure that backups are only connected to known clean devices before starting recovery.
Try GhostVolt Today
Encrypt any document on your computer including your tax returns, photos, movies or any other document
Secure, automated AES encryption.
Prevents Identity and Data theft
Ransomware blackmail protection
Works just like Windows Explorer, but securely
No Credit Card or signup needed
