How Your Passwords End Up for Sale on the Dark Web
Learn how to secure your passwords and avoid personal data theft.

Credential stuffing and similar attacks are made possible by cybercriminals with access to large lists of common and breached passwords. But how do these cybercriminals get these lists of passwords to try? Two of the main methods are via phishing attacks and data breaches.
Phishing Attacks
Phishing attacks are the easiest way for cybercriminals to gain access to account credentials. If a phishing page tricks you into entering your username and password, then these credentials are sent straight to the attacker. They can then add them to a list of credentials for sale on the Dark Web or keep them for their own personal use.
Inside a Data Breach
Data breaches have become a fact of daily life. In the US alone, 1,473 data breaches were reported in 2019. This averages to 4 breaches and over 450,000 breached records per day. In many of these breaches, passwords are listed as part of the exposed data. However, most organizations don’t store their users’ passwords. This would make it far too easy for an attacker or a malicious insider to steal the master password file and use it to gain illegitimate access to user accounts.
Instead, when data breaches talk about passwords being breached, they are actually talking about leaked password hashes. Hash functions are cryptographic operations with a few useful properties:
- One-Way Function: It is impossible to calculate the input to a hash function from the corresponding output.
- Collision-Resistance: It is very difficult to find two inputs that produce the same output.
- Deterministic: Hashing the same input always produces the same output.
These properties make hashes an ideal way to store password data. Instead of storing a list of passwords (which can be abused), a list of hashes is stored instead. When verifying users, if the hash of the password that they provide matches the one on file, then they are likely to have provided the correct password. However, if the password hashes are leaked, then an attacker still doesn’t have the original password.
Professional File Encryption for Everyone
GhostVolt Solo
Secure all your files with enterprise level automated encryption, secure file sharing and much more...

From Password Hashes to Breached Passwords
If password hashes are so secure, then how do data breaches lead to passwords being offered for sale on the Dark Web? This mainly happens when someone has made a mistake.
The less common reason for this is that the breached service is not storing passwords securely. If passwords are not appropriately hashed or are using a broken hash algorithm (like MD5 or SHA1), then an attacker may be able to break the hash and determine the user’s credentials. This isn’t the most common reason that passwords get broken, but it does happen.
More commonly, the fault is on the side of the user. An attacker can take a “guess and check” approach to breaking passwords by hashing potential passwords and comparing them to breached password hashes. If the hashes match, then the attacker has found the right password.
This is what makes the use of weak and reused passwords so dangerous. If a password is easily guessable (based off of a word, pattern, etc.), then password cracking tools will easily be able to identify it in a list of breached password hashes. Once this occurs, the attacker is able to sell the breached password rather than just the hash.
How The Good Guys Are Fighting Back
Most people don’t know when they’ve been the victim of a data breach. For this reason, many online services have incorporated breach notifications. This means that, if you try to log into an account that has been breached or using a breached password, the service will notify you and help you reset the password. In most cases, these breach notifications are driven by HaveIBeenPwned, a site that collates this data and allows people to determine if their data has been breached.
These services work because they use the same tools and techniques as malicious attackers. Cybersecurity researchers search the Dark Web for lists of credentials that have been publicly posted or offered for sale. Any password hashes that they collected can then be subjected to password cracking to determine whether or not they are likely to be broken by attackers. This is where the lists of the “most commonly used passwords” come from.
Applications like GhostVolt also use HaveIBeenPwned to help protect people from reusing breached passwords. When setting a password on GhostVolt, the password is automatically checked against HaveIBeenPwned’s list of breached passwords. If a match is found, GhostVolt will not allow the use of this weak password. While this may seem inconvenient, it is essential to protecting the security of your GhostVolt account.
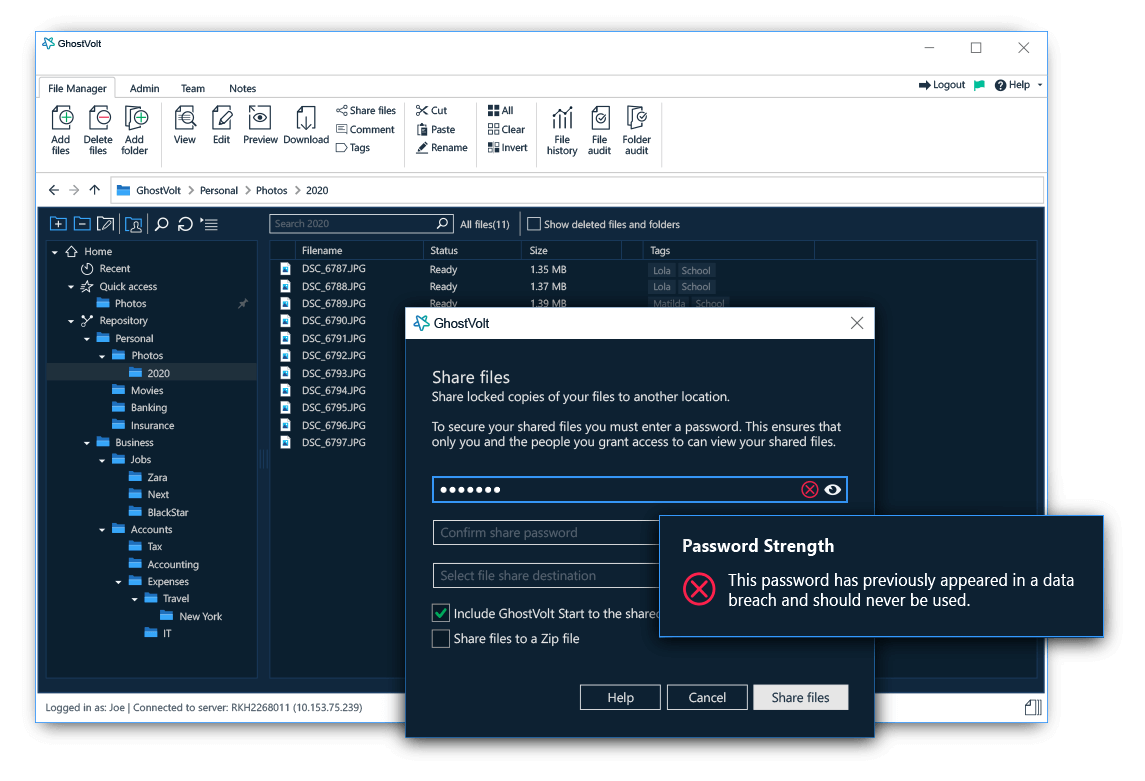
GhostVolt automatically checks your passwords against 600+ million breached passwords.
Protecting Your Online Accounts
If you are notified about a breach of one of your online accounts, it is vital to change the affected password immediately. However, this may be too little too late since a breached account means that attackers already may have access to your account.
Being proactive about password security is a much better idea. Instead of waiting for passwords to be breached, replace any weak and reused passwords with unique, strong ones and store them in a password manager. This dramatically decreases the risk of cybercriminals compromising your account if an online service is breached and password hashes are leaked.
Professional File Encryption for Everyone
GhostVolt Solo
• Enterprise level security
• Secure unlimited files
• Automated encryption
• Secure file sharing
• ... and more

Guest author Howard Poston is a cybersecurity and blockchain security consultant and trainer. You can reach Howard at howard.poston@gmail.com


