The Evolution of AES
Encryption, the practice of securing information from unauthorized access, boasts a rich history that spans centuries. Join us as we delve into the fascinating journey of encryption, tracing its evolution from the time of Julius Caesar to the modern standard known as AES.

Before AES - Encryption's Early Days
Long before encryption was as standardized as it is today, people used a variety of techniques to protect their secrets. For example, the Spartans in ancient times used a clever device called a scytale to send hidden messages during battles. It involved a leather strap wrapped around a wooden rod, with letters that only made sense when wrapped around the correctly sized rod. Julius Caesar had his own method – he shifted letters in the alphabet, like turning A into D or B into E, which was a simple but effective way to keep messages hidden. Fast forward to 1973, and we saw the birth of the Data Encryption Standard (DES), a significant development in the 1970s, but it wasn't perfect. By the late 1990s, DES was vulnerable to attacks due to advances in computing power.
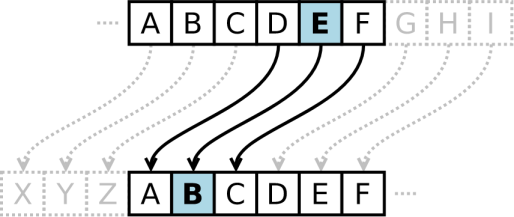
The Caesar cipher
DES
The Data Encryption Standard (DES) is a method to hide digital information. It was created in the 1970s by IBM and became a widely accepted way to keep data safe. DES works by taking blocks of plain text (like a short message) and turning them into secret code using special keys that are 48 bits long. It goes through several steps to do this. While DES was important in the history of keeping information secure, its keys were not long enough to protect data in modern times. That's why we now use the Advanced Encryption Standard (AES) instead.
The Rise of AES Encryption
The Advanced Encryption Standard (AES) came into play in 1998, designed to replace DES. It was created by two Belgian cryptographers, Vincent Rijmen and Joan Daemen. The National Institute of Standards and Technology (NIST) organized a competition to find a more secure encryption standard to carry us into the future, and in 2001, AES emerged as the victor. Before AES, DES was the go-to encryption method, but it had some issues, like a small key size and susceptibility to brute-force attacks. AES improved on these problems by using larger keys and blocks, making it a more secure choice.
The Ubiquitous Role of AES Encryption
The IOT powered by AES
AES encryption plays a pivotal role in safeguarding sensitive information across a wide array of everyday services and applications. Virtually all secure communications over the internet, such as online banking, e-commerce transactions, and email services, rely on AES encryption to ensure the confidentiality and integrity of data. Major cloud storage providers like Google Drive, Dropbox, and Microsoft OneDrive employ AES encryption to protect user data stored in the cloud. Additionally, messaging applications like WhatsApp and Signal use AES encryption to secure user conversations, making it challenging for unauthorized parties to intercept or decipher messages. AES encryption is also integrated into virtual private networks (VPNs), ensuring the privacy of internet traffic. From securing your smartphone's data to enabling secure video conferencing and remote access to corporate networks, AES encryption is an indispensable tool that underpins the privacy and security of everyday digital life.
Looking Ahead: The Future of AES
AES has been protecting data for over 20 years, serving as the encryption standard for nearly two decades. It remains one of the most secure encryption methods available today. However, technology is always advancing, and so are the techniques used to crack encryption. To stay ahead of potential threats, it's crucial to continue refining encryption methods. One major concern is AES's vulnerability to quantum computing attacks. Quantum computers have the potential to break many of today's encryption algorithms, including AES. As a result, researchers are actively working on creating new encryption methods that can withstand quantum computing attacks.
Conclusion
In conclusion, since its introduction in 1998, AES has become a widely adopted standard for securing data in many applications. However, the quest for better encryption must continue, especially in the face of evolving threats as technology advances.
